Chase spends $200M annually on cyber security, and yet they got blind sided with a security breach. If Chase spends $1B annually on cyber security, would that prevent a breach? Probably not, as Chase is already one of the most cyber fortified companies in the world today. Target and Home Depot deployed the best cyber security solutions money could buy, and they suffered the same fate as Chase. The problem is bound to get much worse, as the “Internet of Things” starts taking off. It’s a cat and mouse game between the good guys and the adversaries, and by the looks of it, the adversaries are winning all day long.
New Radical Approach to Cyber Security
What is needed is a new approach to cyber security that is radical, revolutionary, far-reaching, and ahead of its time. Is there a singular, overarching layer of security that can mitigate advanced malware, zero day exploits, DDoS attacks, and phising scams 99% of the time? The answer is Yes, and its possible with the CyberSecurity CDN of 2020. Akamai, EdgeCast, CloudFlare and Incapsula have taken the first step in the right direction. Now they need to take an additional hundred steps forward to get to the point where they can absorb every single type of attack, from anywhere in the world, down to the packet level. It’s complex, but feasible. First let visualize the solution, than discuss it in bullet points down below.
4th Gen CyberSecurity CDN of 2020
Solution to Cyber Security Attacks
In order to accomplish the state of cyber security enlightenment, CyberSecurity CDNs must transform themselves into a completely new company, and develop things we haven’t seen before. Here are a few brainstorming ideas.
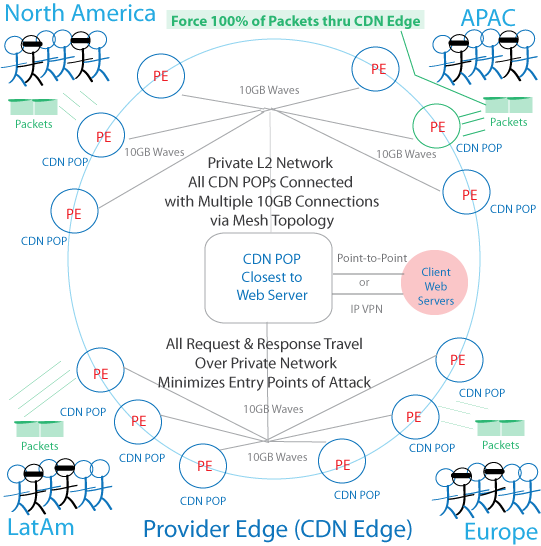
- Deploy global POPs covering all major regions in the world: CyberSecurity CDNs have that in place now
- Forget BGP, UDP, TCP and the upper layer protocols at the core network (PE = Provider Edge)
- Use a layer 2 protocol such as VPLS or Ethernet at the core, to improve delivery performance, and eliminate the need to do look-ups of IP addresses in the routing table
- Connect CDN POPs at the core with 10GB waves, thus creating a truly non-public, private mesh network, similar to MPLS, but with layer 2 non-MPLS technology, thus minimizing the entry points of attack as packets jump hop to hop
- Invent a protocol for the core if need be
- Force every single end user request and response through a CDN POP so the CDN can filter the packet, and track each packet throughout the globe
- CDN will store, and report in real time where each packet travel from origin to destination
- Connect customer HQ to the CDN POP with a point to point connection, or IP-VPN connection
- In the case of retailers like Target, force all retail IP traffic to go through a CDN POP, where the CDN will filter it, clean it up, and send it to its proper destination, not a server located in the other side of the planet
- CDN will encapsulate the packet at the Provider Edge from IP to a L2 protocol
- CDN must develop a VM layer that sits on top of the browser (javascript) so that whenever anyone, whether legitimate or hacker, makes an entry, the CDN can capture the input, and clean it up, sending it along its way, completely neutralizing SQL injections
- 24x7x365 SecOps NOC team that monitors packet travel for each customer
The theme of the 4th Gen CDN is “end-to-end” packet visibility and control. The CyberSecurity CDN will force all requests/response to go through its POPs, where they will be filtered, cleaned up, and tracked in real time, from origin to destination, from one country to the next. Thus, if an adversary decides to install RAM scraper malware at the POS system of Walmart, and is successful, it won’t really matter, because the server in the network that the hacker controls, can only push out traffic through the CDN, where the CDN will clean it up, whether its port 80, 443, or whatever. In a way, its like have a dozen Palo Alto’s and FireEyes in each CDN POP, in POPs located around the world, with a feature that tracks and controls packets.