The Bizety team recently spoke at length with Yuri Frayman, CEO, of Zenedge. If you haven’t been keeping up, we previously published a two-part interview with the company’s CTO Leon Kuperman. This conversation revolved around Zenedge’s ability to protect large enterprises with multiple locations and hundreds of partners in their supply chain, with their newly announced product Zenshield Dome.
Q: Tell me about Zenshield Dome
Frayman: As you know, it’s been almost a year since Target was attacked. The breach occurred in the supply chain where a vendor with access to Target’s network was hacked, which allowed the intruders to gain entry into the Target network. Once in, they exposed system weaknesses and attacked other networks including those that contained sensitive data. A vendor in the supply chain becoming the weakest link in a large company’s cyberdefense is not an unusual scenario. In fact, one out of five companies we talk to connect with a hundred plus partners in their supply chain.
The automotive industry is a good example, as there are literary hundreds of suppliers that feed into the business network of Ford and General Motors. Sure, all these companies and their supply chain have some level of perimeter based security, however, this only secures one part of the supply chain based on different rules, relying on the sophistication of the IT personnel and the capabilities of the systems. In contract, Zenedge Dome protects the large enterprise and its entire supply chain with a common set of rules and security policies.
Zenshield Dome is designed specifically to complement a large enterprise’s perimer-based security with a Cloud-based web application security platform. It not only creates a shield around the large enterprise’s perimeter, but also erects a “dome” around all its partners and suppliers as well. This allows for the large enterprise to set rules and policies that are applied across the Dome, protecting the enterprise and it’s entire ecosystem from cyberattacks..
Q: What does your pricing structure look like?
Frayman: There is a platform fee and a usage fee determined by monthly data transfer measured in GBs/month. The large enterprise pays one fee, while suppliers pay a lower platform fee. In some cases, the large enterprise pays the fee for the entire supply chain. In their opinion, however, the overall fee is negligible compared to the risk of a breach and the resulting financial impact on the company. Our customers pay between five and fifteen thousand monthly depending on the level of protection and bandwidth.
Q: Have you had any interesting conversations with companies? What are their challenges and how can you help?
Frayman: Many customers deploy a security solution for their corporate network that often comes in the form of a firewall, APT platform, or other type of appliance. The challenge, however, is that although an enterprise might have the best defenses in the world, it doesn’t mean that their suppliers will deploy the latest and greatest. In one instance, we talked to a financial institution that had a hundred suppliers who were able to access certain sections of their corporate applications and each one posed a risk to the enterprise. With our solution, the entire consumer supply chain is protected.
Our platform enables an enterprise to set an individual policy for each and every partner in the supply chain. Additionally, we work with different types of traffic such as HTTP, HTTPS and VPN. As you are aware, many large enterprises communicate extensively over VPN, so a standard CDN WAF won’t work in this case.
Q: Interesting. So, not only is Zenedge a B2C platform, but also B2B platform since you work with VPNs. VPNs are prevalent within the Fortune 500, where remote offices and partners communicate with backend applications or web applications located at HQ. Correct?
Frayman: That is exactly right. One of the things that got us into this world was a conversation with a large customer that stated “we buy millions of dollars, worth of products (Palo Alto, Arbor Networks, etc.), but we can’t force our partners to buy the same products, let alone help them hire the right people to manage it.” So, that’s how we arrived at our cloud based security solution.
Besides offering granularity down to the individual partner, alerts can also be set up to notify staff when abnormal traffic is identified via our algorithm based APT engine. The really cool part is that customers can set a specific rule on a particular partner without forcing those rules down to other members in the supply chain. That’s a compelling proposition.
I would just like to highlight that Zenshield Dome allows for threat intelligence to be shared with all partners in the supply chain. This allows better coordination of security policies, while warding off attacks. This hasn’t been done before, but its been talked about.
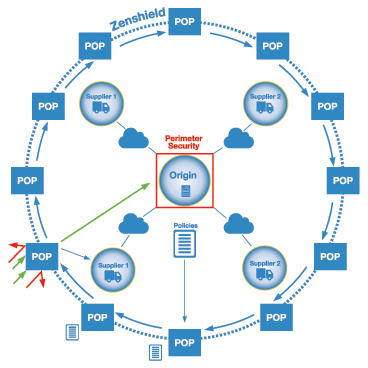
Q: Could you talk about this diagram?
Frayman: Lets say City Bank is the origin and suppliers 1, 2, etc. are companies that have access to corporate applications via the Internet. Zenshield Dome, with its global POPs, shields City Bank and the suppliers in the supply chain. Each supplier has its own on-premise, perimeter-based security. In addition, they share the Zenshield Dome and are protected by a common set of rules and policies that are set by City Bank.