Baidu, Google, and Facebook are deeply invested in deep learning via neural networks, or networks of hardware and software that approximate the web of neurons in the human brain.
The neural networks are essentially large swaths of simulated neurons and synapses (much like the human biological brain) that are capable of recognizing distinct patterns. Through vast amounts of digital data, deep learning can be approximated as neural nets. A large artificial neural network is fed input, such as audio of a certain word or images showing a particular object, and over time this network will “learn” to recognize almost any raw data.
So far, deep learning has been used extensively for voice/face/image recognition or powerful search queries. Companies wanting to discover data that are indicative of a prediction they are trying to make or a piece of data, such as a user or an image, they are trying to label. Deep learning software is capable of automatically finding correlations in the data and allowing the automation to run recognition patterns at the fastest rate.
In addition, high powered GPUs can direct the neural nets to automate these tasks at a much faster rate without requiring more computational power, more hardware, or unique infrastructures. This is why Facebook recently started using Nvidia Tesla M40 GPUs to power their open-source Big Sur hardware. A single Big Sur chassis comprises up to eight Nvidia Tesla M40 cards, and each card has 3072 cores and 12GB of memory, which can allow training their neural networking twice as fast and scale twice as large.
For security firms, deep learning is a promising method for the next generation of malware detection software. The idea is that artificial neural networks can be trained over a period of time to recognize the characteristics of potentially harmful threats. These deep learning systems can be trained by using thousands of raw malware data such as executables, compiled code, documents, or scripts, and then immediately recognize the impending malware.
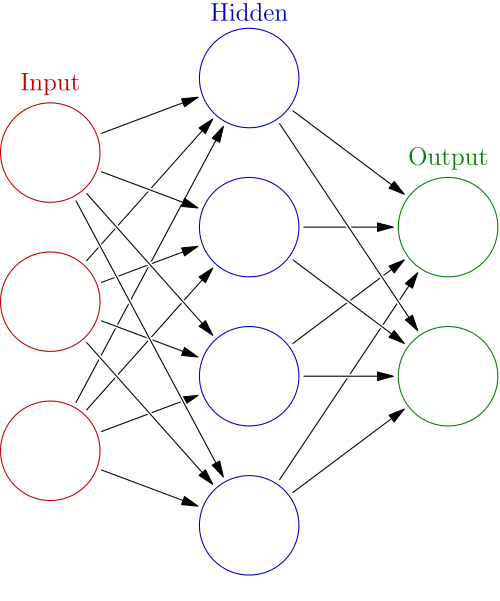
The Power of Deep Learning
The above figure represents an artificial neural network (ANN). A neural net can be shown as the result of spinning classifiers together in a layered web. From the input on the far left side, firing a classifier on the input produces a score on the output. Each node in the hidden and output layers has its own classifier, and will propagate to the next node depending on the data received. The output has a determining score where the results of the classification are determined by the scores at each node. If applied for anti-malware measures, the software can be provided data such as pattern signatures, encryption, etc, data.
Because neural networks are great at recognizing patterns, they can also be trained to generate an output when something occurs that doesn’t fit the pattern. What the neural network already knows about threats and based on the input data, it can “generalize” unseen examples and can output a predictive score to quickly determine if the input is malware.
Applications Threat Morphing
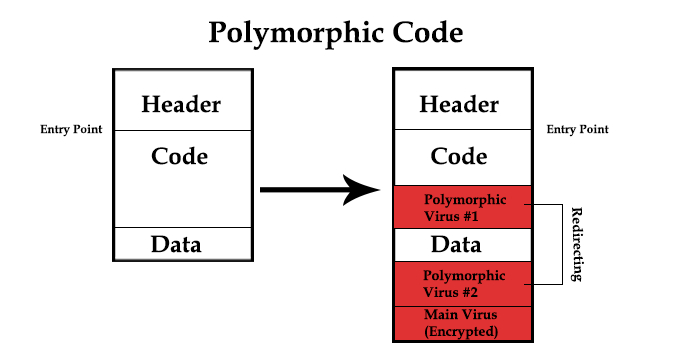
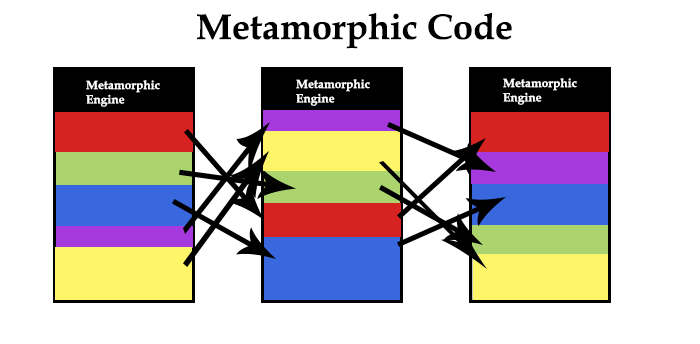
Utilizing deep learning can be useful to recognize threats, and would be especially effective in threat morphing. Polymorphic code infects files with modified and usually encrypted versions of itself, which decrypts before execting. The virus and decryption module are modified, making it difficult to detect. Metamorphic code, a much more complex version of polymorphic, is rewritten with each iteration so that each succeeding version of the code is different from the preceding one. The code changes makes it difficult for signature-based antivirus (AV) programs programs to recognize that different iterations are actually the same malicious code.
AV programs attempt to locate malicious code by searching through computer files and data packets sent over a computer network. However, since it can only detect known malware in its’ source library, polymorphic/metamorphic codes makes it difficult for software to recognize the offensive code since it constantly mutates and adapts into the computer system. Given the enormous volume of unknown files, inspecting the source threat by manually selecting drives and folders is impossible.
Threat morphing can self-learn through replication so the longer it stays in a system, the more sophisticated it can become, and incident response is consequently much slower. AV problems are becoming ineffective against mutating malware, and especially against APT attacks (Advanced Persistent Threats). According to the Verizon 2015 Data Breach report, a total of over 170 million malware events were reported, with 70-90% of the malware samples given were unique to a threat organization. Thus, finding the malware signatures alone are becoming more ineffective.
To combat threat morphing, AV companies could utilize deep learning to automatically detect new instances of malware, especially as newly released iterations are becoming more wholly sophisticated. Most security vendors use machine learning (or more specifically, supervised learning) to deal with the high malware volume that is created each day, applying the same mathematical operations in the same order for every input. Deep learning goes further than machine learning since it uses artificial neural networks to mimic a brain to quickly recognize specific distinctions of malware. If deep learning is applicable to certain software recognitions, then neural nets could identify a new piece of malware just because it looks like other malware.
Researchers are using deep learning algorithms that can spot new malicious code naturally, without database updates. An Invincea study tested the effectiveness of neural networks usage in malware. They used 400,000 software binaries that are either benign or malicious are entered into a deep neural network that comprises of an input layer, two hidden layers, and an output layer. As the binaries enters through the neural network, the output layer determines the score to determine the probability of the file actually being malware. From the results, deep learning recognition software appears to have a high detection rate of zero-day malware with a very low false positive at a reliability of 95 percent and an error rate of .01.
Additionally, a Microsoft study trained several large-scale neural network systems using file strings and application programming interface to classify over 2.6 million labeled samples, with some of samples belonging to 134 malware families. From the results, they were able to classify malware with a two-class error rate of 0.49% for a single neural network and 0.42% for an ensemble of neural networks.
Companies Claiming Deep Learning Solutions
Deep Instinct, an Israeli startup, claims that they are the first to employ offer a deep learning- based AV solution using ANNs. They use data fragmentation by breaking down objects into their smallest parts, and applying deep learning to identify unknown suspicious behavior and detect, predict, and prevent known and unknown threats.
Their deep learning solution comprises of three components: D-Brain provides the real-time cyber threat intelligence that features continuous learning to predict new malware and then update the D-Appliance and D-Clients for what the company says is instant, instinctive protection against never-seen-before threats. They claim that its software is 20% more effective at catching modified versions of existing malware than the best current generation of AV solutions.
Baidu has long been an investor in AI and deep learning, and they are also selling Symantec-like products to Chinese companies using deep learning.
Symantac recently announced integrating deep learning to detect 0-days malware. Android versions of Symantec mobile security products are the first to include deep learning, but will soon spread to other platforms.
Cylance has 1 to 2 PB of data reserved solely for machine learning. Currently in development, they are reported to have used deep learning to train their software to discern malware without the need for sandboxing or analyzing malware.
Conclusions
Deep learning shows a lot of promise as a preventative measure against AI malware and threat morphing. Few deep learning-based malware detection methods so far have achieved the low false positive rates and high scalability required to deliver reliable predictors for threat morphing malware. However, these developments are still quite skeptical since security firms have just wholly embraced integrating deep learning for their software. Until more results are released, it is difficult to determine if a neural net recognizes malware or applications that perform a lot of network activity.
Software companies need to account for the false positive statistics that occur, as previously indicated in the Invincea and Microsoft study. Even if deep learning can recognize suspicious patterns as possible malware, the rate to achieve a very low false positive is extremely difficult. While deep learning has great potential, it needs more time “learning” how to recognize strains of malignant signatures overtime so that it can actually detect threat morphing at a higher accuracy rate without displaying more false positives.
Although deep learning is relatively new in the cybersecurity space, neural nets gives us a wider understanding that traditional methods against malware are becoming more outdated. The implementation is necessary where in the current security landscape, protection requires a quick and fast incident response to determine the overall information of file that has been analyzed; little revision concept like deep learning definitely helps to reduce impractical techniques.

