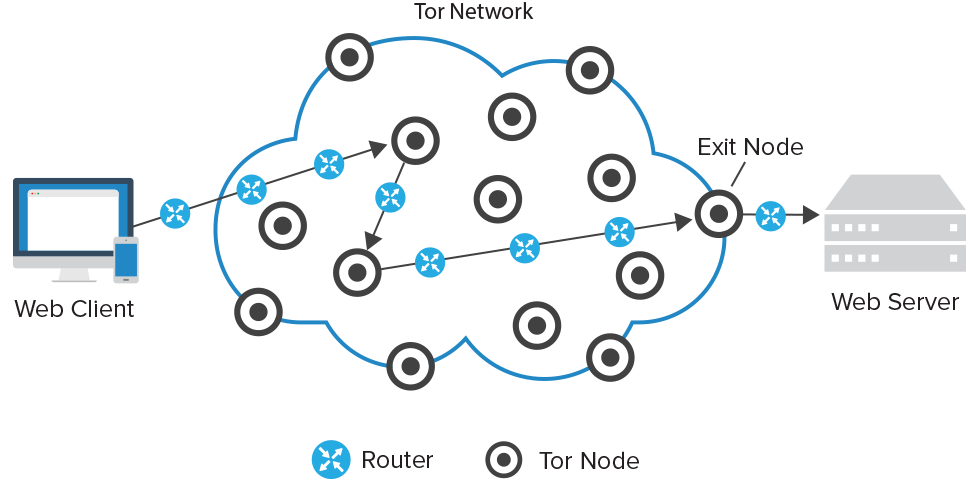
The Onion Network, otherwise known as Tor, is a free, open network browser that specializes in letting you surf the Internet without any form of network surveillance. It gets its name because of the way it routes traffic is like peeling away at layers of an onion. It runs traffic through a number of relays and each one only knows the next hop and not the final destination, passing the information around until it gets to the last node that is connected to the website.
 source: distil networks
source: distil networks
Over the past couple months, though, there has been some debate as to the security of the network and whether it is providing the dignified service that their mission statements endorses. According to the Tor project, their intention with creating a browser where none of your activity is monitored was born out of threats to political dissidents and marginalized people living in primarily third world nations, or under oppressive regimes.
With Tor, people could use the Internet without fear of their government watching them. Even in America, studies show that up to 9% of Americans use Tor or similar measures to help obtain unmonitored Internet access, especially in the wake of the NSA scandal.
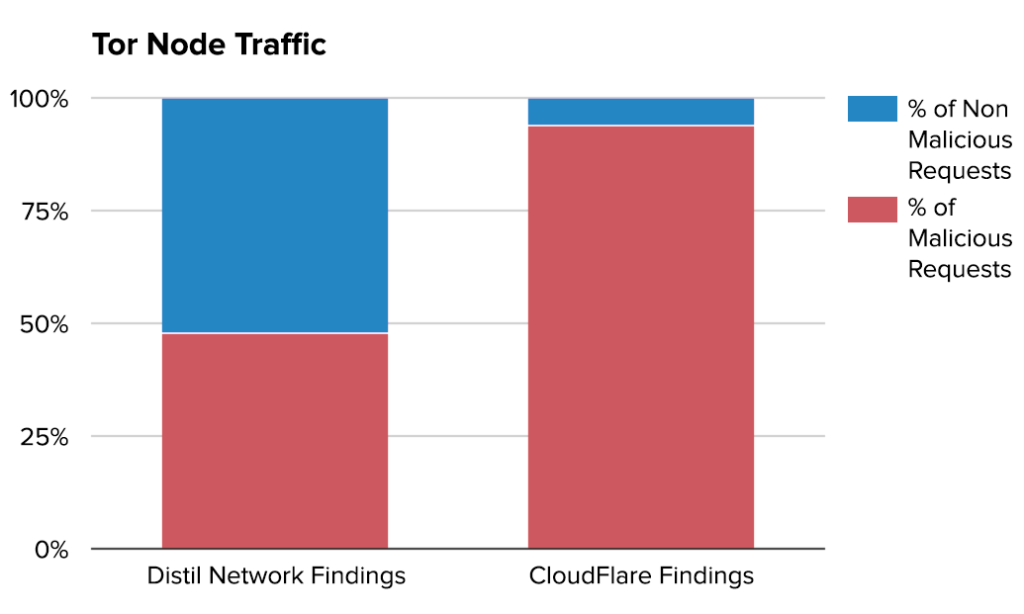
But because of its anonymity, Tor has often enabled illegal activity, such as harboring black market sites like Silk Road. Recently, CloudFlare has gone as far to say that “94% of requests that we see across the Tor network are per se malicious.”
This assertion has caused a lot of skepticism and retorts across the web, with Distil Networks even issuing a counter-report that analyzes the same data and report, concluding“Tor node requests are malicious 48% of the time.” They mentioned that this number was higher than they expected, especially compared to other proxy networks that typically average out to about 38%, but if their findings are correct, that means that CloudFlare is blocking almost half of innocuous Tor users.
The way CloudFlare checks Tor traffic is by using captchas or other restrictions to assign a threat score to the IP, but since multiple users share IPs, CloudFlare is stuck in a Catch-22. They could monitor the individual reputation of specific browsers using a single IP that might be blocked due to other malicious activity that has taken place on it, but then that would be contradicting the point of using Tor, since the appeal is the fact that it is not being monitored or tracked. So what should they do?
Their response has been to block exit nodes of IPs that may issue spam or have potential to cause threats, and this has led to them blocking 94% or Tor traffic.
In their report, Distil Networks points out that while IP blocking is a valid security measure, and that they still use it themselves, that CloudFlare is failing to recognize that attackers often use more than one IP, so their blocking strategy isn’t entirely saving their network, so much as it is just hurting the innocent Tor users. But in their post, Distil offered no other solution for how to combat Tor’s elevated malicious requests, other than to point out that CloudFlare is doing it somewhat poorly. I guess they don’t have an answer to the Catch-22, either.
CloudFlare, though, continues to search for a better way to combat these malicious requests, even suggesting working directly with Tor to help create more long term solutions. Some potential ideas include:
- Captchas that are less inconvenient for humans
- Potentially treat GET requests for static content differently than more risky requests like POSTs
- Allow customers to whitelist Tor exit nodes
- Allow customers to specify rules that apply to traffic specifically from Tor
- Looking for a way to allow automated malicious traffic to be distinguished from non-automated traffic: but this would take help from Tor themselves
- Client-side captchas that move the process of distinguishing between automated and human traffic to the Tor browser itself