Distil Networks released new threat research on mobile bots on Wednesday, revealing how millions of mobile devices, which have been infected by malware, are being used to carry out bot attacks. Emanating from the bot mitigation company’s Research Lab, the new research is based on a 45-day analysis of the mobile devices on its own customer networks, amounting to over 100 million devices in total.
The new report is titled “Mobile Bots: The Evolution of Bad Bots”, and highlights the new trend of mobile devices being put to use in automated attacks by cybercriminals and bot operators. Mobile devices are increasingly being leveraged in an effort to escape detection and execute a series of malicious acts. These include web scraping, online fraud, account hijacking, data theft, brute force attacks, competitive data mining, spam and digital ad fraud.
Distil has labelled the bots as advanced persistent bots (ARB), and found that the APBs can be launched from both mobile devices and laptops used in public places.
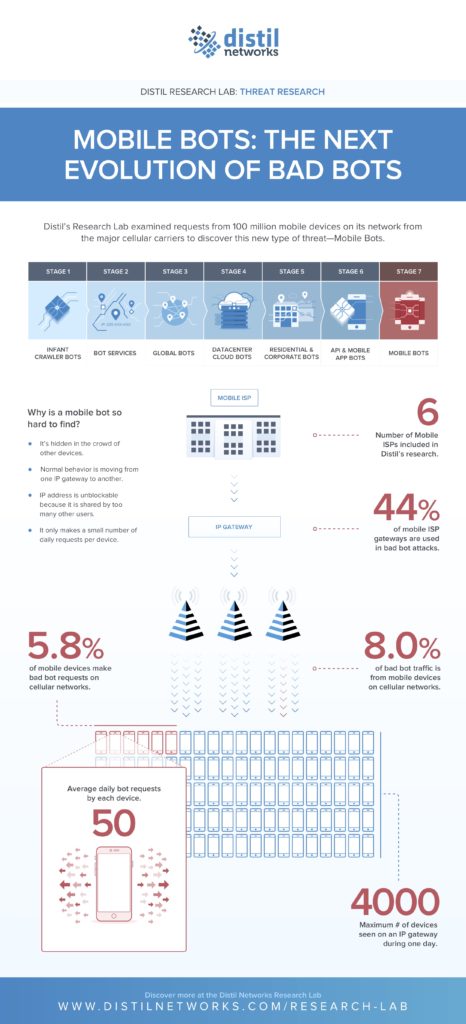
The report’s findings reveal that 5.8% of all mobile devices over six major cellular networks are deployed in bot attacks, constituting 8% of all bad bot traffic.
Using mobile devices represents a new kind of attack method, which offers cybercriminals the advantage of going after multiple websites and apps at the same time via cellular gateways; and a new means of eluding detection. Bot operators are always looking for new ways of getting around defense systems and chameleon-esque disguises to do so.
Distil’s researchers found that 44% of all cellular ISP gateways were used in the mobile bot attacks they surveyed. Cellular gateways are designed for industrial and commercial use. They typically handle a large number of requests per minute, which can make it easy for the mobile bot to stay hidden and hard to detect what is legitimate traffic vs. malicious. A single IP address can serve over 4,000 devices daily within some cellular carriers, meaning that the IP address becomes unblockable as too many users share it at once.
Furthermore, many mobile devices move across multiple gateways in a day as they change locations, meaning that bots are also effectively able to change their identities, making detection even more challenging. Additionally, bot operators place limits on the number of bot requests issued daily in order to make detection more difficult.
Distil found some interesting averages during their 45 day study, which demonstrate the ease of bad bots hiding within otherwise legitimate traffic, including: (i) the average number of daily bot requests per device was only 50; (ii) the maximum number of devices issuing bad bot requests on a single IP daily was 862; (iii) each day, Distil observed 15 devices making bad bot requests on every cellular gateway IP address.
Bots have been continually changing shape since the early 2000s when they began to roam the Internet. Initially, there were only good bots, but they have been increasingly used and transformed into vehicles for fraud and abuse. In its report, Distil identifies seven stages of evolution of the bad bot: (i) Infant Crawler Bots (ii) Bot Services (iii) Global Bots (iv) Datacenter Cloud Bots (v) Residential & Corporate Bots (vi) API & Mobile App Bots (vii) Mobile Bots.
“Mobile is the new frontier for bot operators, as they can perform highly advanced attacks while remaining hidden in plain sight,” said Rami Essaid, co-founder and chief product and strategy officer at Distil Networks. “Whether inadvertently downloaded through an email attachment, or embedded in a seemingly legitimate app, millions of consumers unknowingly carry malware on their devices that allows cybercriminals to conduct bot attacks, abuse and fraud. We have seen bot operators develop and enhance their techniques throughout the years, but the threat to mobile devices is real and growing, and can have detrimental consequences.”
A mobile bot is typically first enabled by infecting a smartphone with malware. This can happen in multiple ways, primarily via malicious email attachments, drive-by downloads (when a link is clicked or a resource loaded, triggering a rogue download) or when malware is embedded in an app that appears to be legitimate – downloaded from a website rather than an app store.
Then command and control servers are able to communicate with and send instructions to the device to execute an attack. Connectivity is enabled via the owner using P2P VPN or proxy services, usually not realizing the potential consequences of this, which effectively offers access to their device in return for using the service.
Distil advises mobile users to avoid infection through the following means:
- Download apps only from trusted, reputable sources
- Do not download surprise email attachments
- Do not click on unknown links, particularly when sent without explanation in a text or email
- Use antivirus protection against malware on your smartphones, particularly Androids
Distil’s research began with the detection of bad bots on just one cellular carrier that led them to undertaking the larger study, which revealed the same behaviour across six major US mobile ISPs. In 2017, Distil came across a new kind of bot called GiftGhostBot, which was defrauding gift card owners. Almost 1,000 websites were targets of the hack. The bot was used to generate possible account numbers of consumers automatically and requesting the balance account of each card number. If a card balance was received (rather than a 1 or a zero) then the attack was successful, allowing the cybercriminals to sell the stolen credentials on the dark web or use them to make a purchase.
To help combat the threat of mobile bots, Distil recently launched two products: Bot Defense for Mobile Apps and Bot Defense for API. At the end of the report, Distil also issue a set of recommendations for ways to detect bad bot activity, including blocking or CAPTCHA outdated user agents/browsers, protecting bad bot access points and careful evaluation of traffic sources.
The full report can be accessed here: https://resources.distilnetworks.com/whitepapers/research-lab-mobile-bots

