In the ‘DevOps’ world, Ansible, Terraform, Chef, Saltstack, and Puppet are industry-wide configuration management tools. These tools help DevOps create, scale, and manage server configurations with ease.
Before DevOps became prevalent, operations and development were two separate silos. In the pre-cloud era, servers were provisioned and managed manually which was a time-consuming task.
Today, DevOps Pulse 2016 report states that 40% of surveyed participants can deploy code multiple times a week. This is all thanks to automation and orchestration. And, configuration management tools help overcome many problems with automation.
What is the difference between Ansible, Chef, Puppet, SaltStack, and Terraform? Let’s start by pointing out the differences between automation and orchestration.
Automation and orchestration play a critical role in business processes. Regardless of where your data is stored, on-premise, or in the cloud, these tools provide a single platform for all complex business processes to run seamlessly.
IT Orchestration
Orchestration largely involves integration and scheduling automated tasks, in large-scale virtual environments, between complex distributed systems. It streamlines interconnected workloads and operations.
Orchestration tools allow you to automate the management and coordination of complex services, computer systems, and middleware within a computing environment.
IT Automation
Automation takes orchestration one step further. It generally means completing a single task without human intervention. It makes time-intensive, manual processes faster, reliable, and more efficient.
Orchestration uses automation to systematically execute large workflows by consistently managing and coordinating multiple automated processes across separate teams and functions.
In IT, you can automate virtually all processes for both on-premise and cloud functions. For instance, in cloud automation, you can use machine learning for asset management in the cloud.
Comparing the IT Automation and Orchestration Tools
Ansible
Ansible is a simple-to-use configuration management tool that provides powerful automation for continuous cross-platform computer support. Besides, it is more of a provisioning and deployment tool.
Primarily useful to IT professionals, Ansible helps with application deployment, cloud provisioning, configuration management, and virtually everything a systems administrator does on a daily or weekly basis. Its architecture is composed of modules, plugins, inventories, APIs, and playbooks that are like instruction manuals.
While modules help accomplish a task, you learn how to execute modules using an Ansible playbook. The Ansible playbook is a configuration file that is written in YAML. It provides instructions for everything required to bring a managed node into the desired state.
How Ansible Works
When it comes to Ansible, you have two computer categories – managed nodes and control nodes. Managed nodes refer to the devices that are managed by the control node. On the other hand, control nodes refer to the computers that run Ansible.
This IT automation tool connects nodes, which includes all entities in your configuration on a network. Then, it sends a small program termed as the Ansible module to that node. The tool executes Ansible modules over SSH and removes them once the execution is finished.
For this interaction, the Ansible control node should be able to login to the managed nodes via SSH, the most common way to do so.
Key features of Ansible
- Since the tool does not rely on software agents and has no extra security infrastructure, it is very easy to implement.
- Lets you model even the most complex IT workflows.
- Flexible enough to orchestrate the entire application environment.
- This agentless tool does not need any software or firewall ports on the target client system.
Since Ansible is a command-line only tool, it lacks an interactive and user-friendly interface. Unlike comparable tools, Ansible lacks a notion of state. It does not track dependencies, and executes a series of tasks, stopping when finished, fails or encounters an error.
Chef
Chef’s Ruby DSL is excellent for teams composed of a mix of software developers and DevOps engineers who use Ruby for their work.
Another part where Chef outperforms Ansible is its flexibility. The DSL composes Chef cookbooks, recipes, and embedded Ruby templates that together allow for advanced customization for configuration files. Recently, the company has added InSpec and Habitat to the tool, renaming it as Chef Automate.
Chef Automate is a suite of enterprise capabilities designed for node visibility, workflow management, and compliance. It also integrates support services for the entire platform and includes a pipeline for continuous delivery of applications and infrastructure.
How Chef Works
Users interact with Chef at the Chef DK (development kit) workstation, where the author test cookbooks with tools, including Test Kitchen. Users use the command line tools to interact with the Chef server.
Chef server acts as a configuration data hub. It stores cookbooks, metadata that describes each registered node, and the policies applicable to nodes.
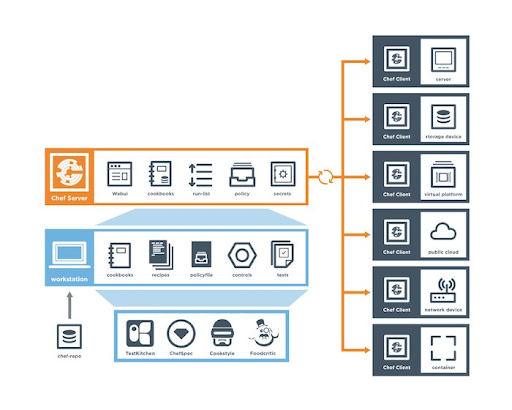
Source: Chef
Nodes interact with the Chef server via the Chef client for configuration details, such as templates, recipes, and file distributions.
In Chef’s architecture, InSpec is an open-source framework for auditing your infrastructure and applications. It integrates with Ansible, Puppet, and Chef. Habitat is another open-source, application lifecycle management, and cloud-native application automation platform.
A recipe can include multiple resources that help in managing and configuring the infrastructure. For instance, the package resource manages packages on a node, while cron edits existing cron files on the node.
Key features of Chef
- It uses domain-specific language based on Ruby programming language.
- It is suitable for complex cloud deployment across platforms, software, and storage.
- Instead of making assumptions, it uses mechanisms to retrieve the current status of the machine.
- Easily integrates with any cloud technologies that make it ideal for multi-cloud environments.
Note that Chef is currently a good fit for the AWS cloud. It lacks documentation and can be difficult to learn for those who are not familiar with the Ruby language.
Puppet
When it comes to ease of access, Puppet is a good alternative to Chef and Ansible. Puppet uses a master-slave architecture, providing clients with privileges to configure the puppet server for the Client machine and Master machine.
In addition, Puppet’s configuration language is suitable for system administrators. The tool supports only Embedded Ruby (ERB) and Domain Specific Language (DSL).
This DevOps program helps you manage multiple servers. You can define the configuration a system requires and maintain a particular state after the initial setup. Using the Puppet Enterprise product, you can acquire orchestration capabilities.
How Puppet Works
DevOps define configuration parameters for a specific infrastructure using a declarative Domain Specific Language (DSL). Puppet finds out information about a system with the help of a utility termed as Facter. Facter is installed at the time you install the Puppet software package.
The Puppet Master manages important configuration details for all nodes that it controls using Puppet Manifests. Nodes controlled by master have Puppet installed on them. They run a daemon called Puppet agent.
The configuration information is sent to the Puppet master that compiles a catalog depending on the node’s configuration. Nodes use that information to apply required configuration updates to itself.
In the pull mode, agents poll the master to retrieve node- and site-specific configurations. Managed nodes run the Puppet agent application.
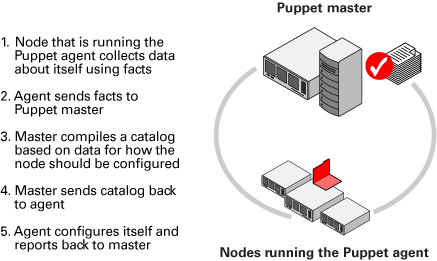
Source: Oracle
Key features of Puppet
- In comparison to Chef, Puppet provides more support for platforms, including Microsoft Windows, Debian / Ubuntu, MACOS X server, Fedora, Redhat, and Centos.
- Since Puppet supports Idempotency, you can safely perform the same settings multiple times on the same machine.
- Puppet has the largest open-source developer base and is used by top brands including Google, Redhat, Stanford University, to name a few.
- Unlike many other configuration management tools, Puppet continuously verifies the configuration at a specific interval and makes modifications as necessary.
Saltstack
Saltstack stands out in this comparison debate in that it is a powerful and robust remote execution tool. Also, there are no juggling SSL certificates as each host has its own private and public key.
Like Ansible, SaltStack also uses administrator-oriented YAML, making it easy to learn the configuration and management of servers.
Another top reasons why DevOps prefer SaltStack are the ease of configuration style and a proactive developer community that is quick to fix any bugs.
How SaltStack Works
Salt Master and Salt Minion are two core components of the SaltStack ecosystem.
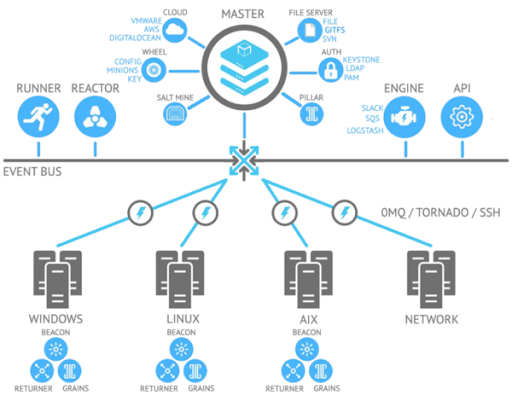
Source: Mirantis
They interact using the ZeroMQ messaging library. This extremely high-performance communication allows this open-source platform to send data at rapid speeds. The ZeroMQ library is available natively in the salt-master and salt-minion daemons.
While communicating, Salt uses a public key to authenticate masters and minions. During the first boot, a minion sends a key pair to the master server it is intended to contact. The master verifies the minion’s identity and accepts the key. Then, master and minion communicate securely using ZeroMQ encrypted with public keys.
In case, it is impossible to install the salt-minion daemon on a particular node, Salt issues commands over SSH that degrades performance considerably. Users are advised to use the salt-minion daemon for security, performance, and simplicity.
Key Features of SaltStack
- One of the most powerful features of Salt is that it can react to events using the Salt Reactor system. Users can configure Salt Reactor to take pre-specified actions according to certain event criteria.
- Salt Cloud integrates with dozens of public and private cloud providers, including Google Cloud Platform and AWS. So, you can easily take inventory of all assets across providers with a single command.
- It supports agentless mode for assets that do not have Salt Minions.
- You can configure Salt Minions to monitor processes, files, services, and a lot of other things.
Terraform
Terraform lets you safely automate and manage your infrastructure. It codifies APIs into declarative configuration files that can be treated as edited, reviewed, and versioned code.
Unlike Chef and Puppet that require installing an agent server at each server, Terraform does not require extra agents. It is the only sophisticated tool that entirely platforms agnostic and supports other servicers, compared to many of its alternatives that are focused on a single cloud provider.
With its plan command, you can review all the changes before you apply them. Code reuse features make Terraform faster than similar configuration management tools.
How Terraform Works
Terraform is divided into two parts: Terraform Core and Terraform Plugins. Terraform Core is a statically-compiled binary program written in the Go programming language. It uses remote procedure calls (RPC) for communication with Terraform Plugins and facilitates several ways to find and load plugins.
Terraform Plugins is mainly responsible for initializing included libraries for making API calls. It also handles authentication with the infrastructure provider and defines resources that map to specific services.
Terraform uses a high-level configuration syntax to define the infrastructure as code. It provides a blueprint of the datacenter to be versioned. Moreover, infrastructure can be re-used and shared.
Key Features of Terraform
- Terraform creates a graph of all resources, and parallelizes the creation of non-dependent resources. It allows Terraform to build highly-efficient infrastructures while providing operators with insights into infrastructural dependencies.
- Due to the execution plan, you can avoid any surprises when Terraform manipulates infrastructure.
- Since it provisions immutable infrastructure, the existing configuration is replaced with the new one with each change and the infrastructure is re-provisioned.
Summary
Basically, there are very few differences between these five configuration tools. But, a single advancement can make a huge difference to your infrastructure. IT users should carefully evaluate each tool to decide which fits best with their environment.
Some act purely as configuration management platforms, while others, including HashiCorp Terraform provide extra capabilities.
Each tool has its own pros and cons, most of which depend on the development language they use, while many are specific to the environment that will use them. You must shortlist configuration management tools based on your unique business needs and then choose the right one.

