Border Gateway Protocol (BGP) is the lifeblood of the Internet. At the most basic level, routers share network information between autonomous systems. It was designed by “Yakov Rekhter of IBM and Kirk Lougheed of Cisco” in 1989.
As of August 2019, more than 92,000 ASNs have been registered. Autonomous System (AS) architecture was introduced to address the many problems inherent in running a highly interconnected global routing system.
Finding the ideal routing platform is important to ISP’s, cloud providers, and CDNs. There are commercial options like those of Cisco and Juniper, which are proprietary in nature and plenty of open source tools available to choose from. CDNs like Cloudflare love open source and they decided on BIRD a few years ago.
Some of the popular open-source tools are Quagga, BIRD, and ExaBGP. However, there are more out there like OpenBGPD and FRRouting which we’ll highlight below. The good news, there’s a multitude of options available for different use cases including one focused on Kubernetes. By the way, ARTEMIS is an open-source real-time detection tool that helps mitigate hijacking, a very big problem in the world of BGP.
OpenBGPD
Claudia Jecker launched OpenBGPD in 2003, mostly as a replacement to the open-source tool Zebra that had various issues and instability.
Jecker added advanced features to OpenBGPD such as neighbor templates as a way of configuration using special kinds of macros to make filters generic. Thus, there is no need to add special filter blocks for each and every peering that is added.
Because of that, it was possible to run route service with very little administrative maintenance. At present, OpenBGPD has all the important protocol features required for running BGP.
Components of OpenBGPD
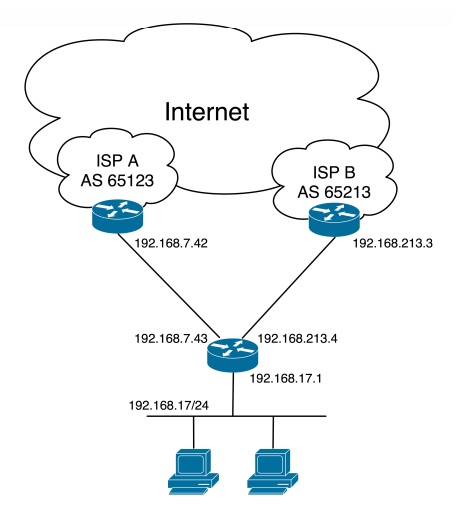
Multi-homing is critical for a successful BGP setup which has independent uplinks via different ISPs to give maximum redundancy. In case, one ISP fails, the other link remains unaffected. That’s when BGP enters. It considers uplink ISPs and calculates the full routine table. If one link fails, the traffic flows via a different link.
As prerequisites, you need a provider-independent address space and an AS number that are available from the local RIRs, or you can obtain these from your ISP.
 Source: OpenBSD
Source: OpenBSD
With all the required information, you can easily configure OpenBGPD. The config file has three sections: global configuration, neighbor configuration, and filters.
OpenBGPD consists of three processes:
- Parent Process
- Session Engine
- Route Decision Engine
Other components of OpenBGPD include Routing Information Base, Forward Information Base, and System Scheduler.
The Parent Process in OpenBGPD is responsible for all the configurations and interaction with the Kernel Routing Table. It has all the privileges to update the routing table.
The Session Engine manages the communication between the neighboring devices to send the “keep-alive” messages. These messages are to verify that the links between the devices are operating.
The Route Decision Engine helps gather all the necessary updates where they are filtered, and calculations are done.
Users of OpenBGPD
The Amsterdam Internet Exchange (AMS-IX), one of the world’s largest Internet Exchanges, deployed two OpenBGPD route servers in 2009. Each server runs more than 350 route server-client sessions, announcing more than 38000.
Net Fonds, a Norwegian internet stockbroker, switched from Zebra to OpenBGPD that the stockbroker found highly stable.
For Japan’s NTT Communications Global IP Network, OpenBGPD provides reliability and security to ensure continued success. Similarly, INFOM-IEO Campus, an Italian research institute, is very pleased with the outstanding performance of the open-source tool. The list of satisfied users of OpenBGPD is surprisingly lengthy.
Developers of OpenBGPD
Henning Brauer, Peter Hessler, and Claudio Jeker developed this popular and useful open-source tool. However, Claudio Jeker manages the portable version of the OpenBGPD tool. It is available with the help of periodic tarball releases.
FRRouting
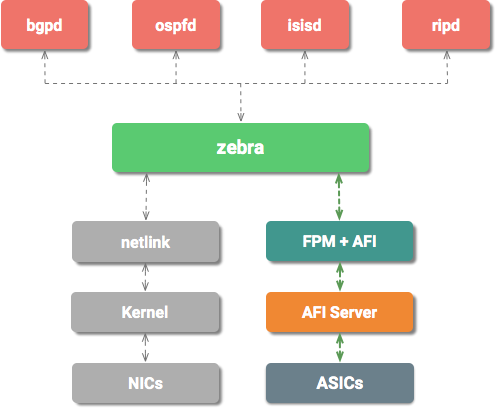
Developed using the fundamental C language, FRRouting is an IP Routing Protocol that helps in determining the route of the data to travel from source to destination through various networks. It is a network routing software suite that provides implementations of different routing protocols like BGP.
FRRouting makes it possible to exchange routing information among other routers. It makes sure that the right data gets updated in the respective routing table.
Source: Juniper
Components of FRRouting
FRRouting mainly comprises C language, but other modules and extensions have used C++ to define its headers files. It has taken over its design architecture from a project called “Quagga.”
One of the primary components of FRRouting is multithreading. It comprises a structure called thread-master, which is a context that keeps track of pending as well as currently executing tasks.
Unlike traditional routing, FRRouting makes use of a collection of daemons to build the routing table. Therefore, it consists of a FRRouting terminal interface to give a glimpse of the routing table information.
Users of FRRouting
FRRouting is an ideal platform for data centers and it provides strong security. Similarly, businesses can use it to connect hosts, virtual machines, and advertising network service endpoints resulting in better performance.
Developers of FRRouting
Known for having its roots from the Quagga project, FRRouting was developed by Quagga developers.
XORP
XORP is a fully-featured open source routing platform that supports IPv4 and IPv6. It gets its name from the extensible Open Router Platform. XORP’s architecture helps in extending protocols with its features and functionality, supporting custom hardware and software forwarding. Also, it supports the following protocols: RIP, OSPF, OLSR, PIM, VRRP, IGMP, and BGP.
Components of XORP
XORP consists of two subsystems – the Higher Level and Lower Level subsystem.
The higher level subsystem consists of the protocol itself, which deals with the routing information bases. It is also called a user-level subsystem. On the other hand, the lower level subsystem manages the path through which the packet travels to reach the destination. It also provides APIs for the better functioning of the higher level subsystem.
Other components of XORP include XORP Resource Locators and Click Modular Router. XORP uses one process for every routing protocol, while other processes are assigned for management and coordination. XORP Resource Locators are used to enable communication between these processes.
Users of XORP
XORP was initially selected for commercial use as a routing platform for the Vyatta line of products. Its users may vary from anyone who is in the networks team, university, and community network groups or data centers.
Developers of XORP
Mark Handley founded the XORP project in 2000, and later it was run by Atanu Ghosh of the International Computer Science Institute.
Kube-Router
Before jumping on to Kube-Router, it is important to know a little about Kubernetes.
Kubernetes is an open-source platform that automates application deployment, scaling, and management. Kube-Router helps in simplifying the operations for Kubernetes clusters. In traditional Kubernetes, you need to install components for various functionalities which are not always effective.
Thus Kube-Router provides easy alternatives of components used for better performance. It has a small code base that is easy to update and maintain. It handles Pod networking using BGP protocol and other libraries.
 Source: Kube-Router
Source: Kube-Router
Components of Kube-Router
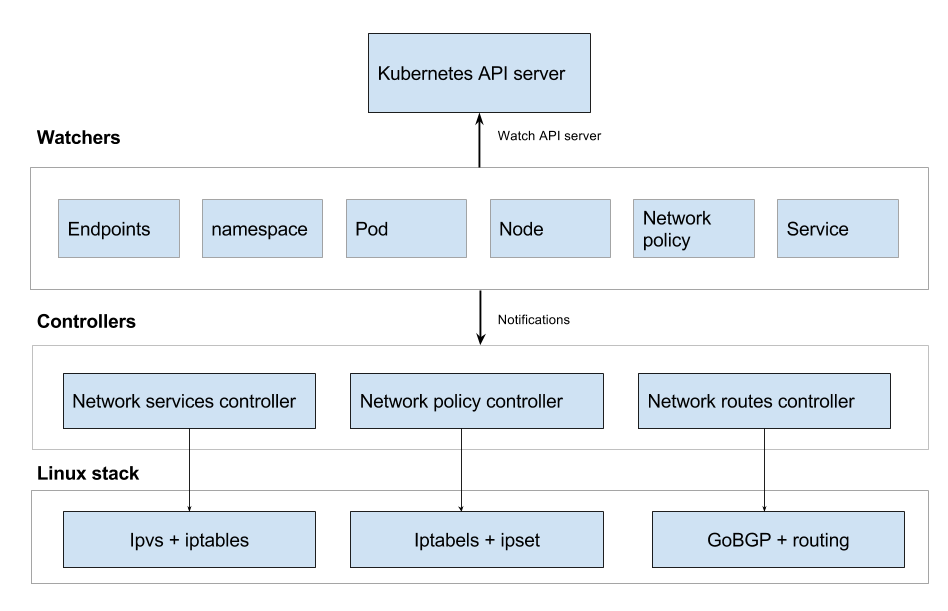
Kube-Router uses the Linux kernel’s features to provide service proxy. The Kube-Router components include Linux Virtual Servers, which are used to implement proxy or direct routing across the network nodes. It provides scheduling options and features like Direct Server Return with the help of Linux Virtual Servers and IP Virtual Servers.
Kube-router consists of controllers and watchers. Watchers use the API to get notification related to events like create, update and delete Kubernetes objects. Every watcher gets notified of a particular API object. On the other hand, controllers register to get notification of the event update so it can act on the events.
Users of Kube-router
Many large enterprises are embracing Kube-Router. Other organizations using the tool included financial firms, universities, data centers, and gaming companies.
Developers of Kube-Router
The creators of Kubernetes developed Kube-Router to work efficiently within that platform.
Vrnetlab
There isn’t much information on this tool. From what we could tell, Vrnetlab is not a fully-featured routing system but a network emulator that runs virtual routers using KVM and Docker. The tool provides an interconnection between virtual routers in a user-defined topology. It was designed to help engineers in the areas of development and testing.
Components of Vrnetlab
The two main components of Vrnetlab are KVM and Docker. Vrnetlab uses the KVM to run a virtual machine while Docker helps manage the network communication between nodes. The tool helps collect all the scripts required to start the router and connect to the virtual environment.
Users of Vrnetlab
Vrnetlab has many users ranging from network engineers to software developers who develop and test the routing process. In addition to this, they also look after the integration process for testing the network bandwidth in a virtual environment. Researchers may also use the command-line interface to experiment in the emulation lab.
Developers of Vrnetlab
Vernetlab was developed by Deutsche Telekom for testing the network provisioning system.
ARTEMIS
ARTEMIS is a highly-reliable tool that provides protection against BGP prefix hijacking attacks. This open-source tool offers fast and accurate detection, by leveraging publicly available BGP monitoring services. It also enables flexible mitigation of hijacking events.
ARTEMIS derived its name from Automatic and Real-Time Detection and Mitigation System. As the name itself suggests, ARTEMIS helps in the detection of attacks and is engineered enough to solve it within minutes. It performs real-time monitoring of BGP updates. For monitoring, it uses BGP streaming service from the RIPE NCC’s Routing Information System, CAIDA BMP feeds, and RouteViews.
ARTEMIS accurately detects BGP prefix hijacking attacks, within a few seconds just after they are initiated.
Components of ARTEMIS
ARTEMIS consists of three components: Monitoring, Detection, and Mitigation.
The monitoring service runs and collects information regarding Autonomous Systems. It provides updates regarding the accurate functioning of the prefixes and ASNs.
The detection service analyzes the collected information from sources and keeps track of the response time. It calculates the minimum delay of the detection service and takes action accordingly.
The mitigation service starts performing its functions as soon as any prefix hijacking is detected. ARTEMIS signals the BGP to converge at the time of mitigation. Once the BGP is converged, the traffic flows back normally.
Users of ARTEMIS
Researchers and network engineers use ARTEMIS to learn the art of mitigating prefix hijacking. Since hijacks can have a large impact, it is important to practice mitigation. Many businesses and authorities have been using this product to prepare a shield from prefix hijacking.
For network operators, ARTEMIS serves as an easy-to-use open-source tool to identify and counter BGP hijacking attacks in real-time against its own prefixes.
ARTEMIS has been successfully tested and deployed in many real-world environments, such as
- AMS-IX, a leading European Internet eXchange Points.
- Internet2, the largest US-based R&E network that provides network services to hundreds of thousands of R&E institutes.
- FORTH, a stub dual-homed academic network that serves Greece’s largest research institutes.
In the immediate future, ARTEMIS will be tested in Europe’s two IXPs: DE-CIX and AMS-IX, as well as US-based R&E networks.
Developers of ARTEMIS
The INSPIRE group at the Institute of Computer Science of the FORTH developed this system and also maintains it.
Summary
There are several open-source BGP tools available in the market. No single tool is best for all uses cases. Telcos and carriers have different needs than a CDN. These tools are an important part of the Internet ecosystem that any company can use, from the startup to the large enterprise. The one major benefit of using an open-source BGP platform, there isn’t a need to spend hundreds of thousands of dollars on proprietary hardware to run a global network.

