Web application firewall
Topics
What is a Web Application Firewall?
A web application firewall (WAF) is a security tool that monitors, filters, and blocks incoming HTTP traffic to a web application. Its purpose is to protect web applications from attacks that compromise their functionality, data integrity, or availability.
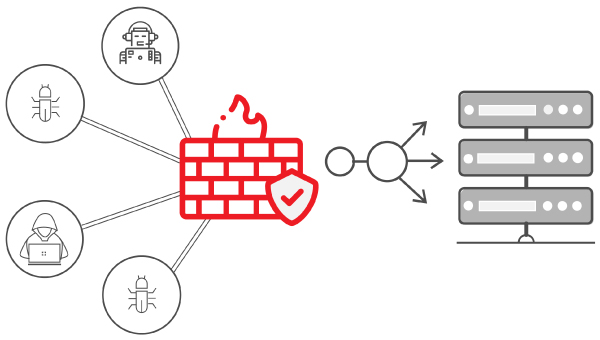
WAFs work by analyzing the incoming traffic to a web application and comparing it to a set of rules or patterns. If the traffic matches a known attack pattern or violates a security policy, the WAF will block the request and prevent it from reaching the web application. WAFs can be deployed as hardware appliances, software programs, or cloud-based services.
WAFs are commonly used to protect against web-based attacks such as SQL injection, cross-site scripting (XSS), and remote file inclusion (RFI). They can also be configured to protect against more sophisticated attacks such as distributed denial of service (DDoS) and botnets.
Overall, WAFs are an important security tool for protecting web applications and the data they handle. They can complement other security measures such as secure coding practices, regular security assessments, and incident response planning.
What are the different types of WAFs?
There are several different types of web application firewalls (WAFs), including:
- Network-level WAFs: These WAFs operate at the network level, inspecting all traffic coming into a network and blocking malicious requests before they reach the web application.
- Host-based WAFs: These WAFs are installed on the same server as the web application and monitor traffic to and from the web application.
- Cloud-based WAFs: These WAFs are delivered as a cloud-based service and protect web applications from attacks by analyzing traffic at the network level before it reaches the web application.
- Hardware-based WAFs: These WAFs are physical appliances that are installed in the network to inspect and filter incoming traffic to a web application.
- Software-based WAFs: These WAFs are software programs that can be installed on a server or in the cloud to protect a web application from attacks.
- Overall, the choice of a WAF will depend on the specific needs and constraints of an organization, including the type and size of the web application, the level of security required, and the available resources for deployment and maintenance.
How does a WAF use machine learning?
Some web application firewalls (WAFs) use machine learning algorithms to analyze and classify incoming traffic. These algorithms can be trained on data sets of known good and bad traffic, allowing the WAF to learn and recognize patterns that may indicate an attack.
For example, a WAF using machine learning may be trained to recognize patterns of traffic that are typical of a distributed denial of services (DDoS) attack, such as a high volume of requests from a single IP address or a large number of requests with similar payloads. The WAF can then use this knowledge to block or rate-limit such traffic, helping to protect the web application from attack.
Machine learning-based WAFs can be particularly useful for detecting and mitigating new or previously unseen attacks, as they can quickly adapt and learn from incoming traffic. However, it’s important to note that WAFs that use machine learning still require ongoing maintenance and monitoring to ensure that they are accurately detecting and blocking malicious traffic.
What is ModSecurity
ModSecurity is an open-source web application firewall (WAF) that is designed to protect web applications from a variety of attacks, including cross-site scripting (XSS), SQL injection, and remote file inclusion (RFI). It is implemented as a module for the Apache HTTP Server and can be used to secure web applications built on various platforms, including PHP, Python, and Ruby.
ModSecurity features several capabilities to help protect web applications, including:
- Real-time request and response analysis: ModSecurity analyzes incoming traffic to a web application and compares it to a set of rules or patterns to identify potentially malicious requests. It can also analyze the responses sent by the web application to ensure that they are not revealing sensitive information or exposing vulnerabilities.
- Custom rules: ModSecurity allows users to create rules to match specific traffic patterns and take appropriate action, such as blocking the request or logging an alert.
- Attack detection and prevention: ModSecurity can be configured to detect and prevent various attacks, including cross-site scripting, SQL injection, and remote file inclusion.
- Auditing and logging: ModSecurity can be configured to log all traffic to a web application, including requests, responses, and any actions the WAF takes. This can be useful for identifying and debugging issues, as well as for compliance and auditing purposes.
Overall, ModSecurity is a powerful tool for protecting web applications from various attacks. It is widely used and well-respected in the security community and has a large user base and active development community.
What techniques do attackers use to bypass a web application firewall?
There are several techniques that attackers may use to bypass a web application firewall (WAF):
- Encoding and obfuscation: Attackers may encode or obfuscate their payloads to bypass WAF rules designed to detect and block specific traffic patterns. For example, an attacker may use URL encoding or base64 encoding to encode their payload, making it harder for the WAF to recognize as malicious.
- HTTP protocol evasion: Attackers may use HTTP request smuggling or HTTP response splitting to bypass WAF rules designed to inspect and block specific types of HTTP traffic.
- Using valid credentials: Attackers may use valid credentials to authenticate themselves to a web application and bypass the WAF’s authentication controls.
- Targeting known vulnerabilities: Attackers may attempt to exploit known vulnerabilities in a web application or the WAF itself to bypass its protections.
- Using SSL/TLS encryption: If a WAF is not configured to decrypt and inspect encrypted traffic, attackers may use SSL/TLS encryption to hide their attacks from the WAF.
- Overall, it is important for organizations to regularly update and maintain their WAF to ensure that it can detect and block a wide range of attacks effectively. This may include deploying new rules or patterns to detect emerging threats, as well as keeping the WAF software and hardware up to date with the latest security patches and updates.
How can users protect against these threats?
There are several steps that organizations can take to protect against attackers who try to bypass a web application firewall (WAF):
Regularly update and maintain the WAF: It is important to keep the WAF software and hardware up to date with the latest security patches and updates. This can help ensure that the WAF can effectively detect and block a wide range of attacks, including those that try to bypass the WAF.
Use a multi-layered defense: A WAF should not be the only security measure to protect a web application. Instead, organizations should use a multi-layered approach that includes secure coding practices, regular security assessments, and incident response planning.
Configure the WAF to decrypt and inspect encrypted traffic: If attackers are using SSL/TLS encryption to hide their attacks, the WAF will not be able to detect and block them unless it is configured to decrypt and inspect encrypted traffic.
Regularly review and update WAF rules: It is important to regularly review and update the rules and patterns used by the WAF to ensure that they are effective at detecting and blocking a wide range of attacks. This may include adding new rules to detect emerging threats, as well as testing existing rules to ensure that they are functioning correctly.
Use a WAF with machine learning capabilities: Some WAFs use machine learning algorithms to learn and adapt to new types of attacks in real time. This can help protect against attackers who try to bypass the WAF by using novel or previously unseen tactics.
How will quantum computing defeat cryptography?
Quantum computers have the potential to break certain types of cryptography, which could have significant implications for the security of modern communication systems. Cryptography is the practice of encoding and decoding messages to protect the information’s confidentiality, integrity, and authenticity. It relies on mathematical algorithms and keys to encode and decode messages, and these algorithms and keys are designed to be computationally infeasible to break.
However, quantum computers have the potential to perform certain calculations much faster than classical computers. This includes certain types of mathematical operations used in cryptography, such as factoring large numbers. If a quantum computer could factorize a large number (such as the one used in the RSA algorithm) in a reasonable amount of time, it could potentially be used to break the encryption and reveal the message.
It is important to note that not all cryptographic algorithms are vulnerable to quantum attacks. Some algorithms, such as those based on elliptic curve cryptography, are believed to be resistant to quantum attacks. Additionally, it is currently not clear when practical quantum computers will be available or whether they will be able to perform the necessary calculations to break certain cryptographic algorithms.
Overall, while quantum computers do have the potential to defeat certain types of cryptography, it is likely that new cryptographic algorithms and protocols will be developed to address this threat as quantum computers become more powerful.
What can be done to protect cryptography from quantum computing?
Quantum computers have the potential to break certain types of classical cryptography, which could have significant implications for the security of modern communication systems. In response to this threat, researchers and practitioners are developing new cryptographic algorithms and protocols that are designed to be resistant to quantum attacks. These algorithms and protocols are often called “quantum-safe” or “post-quantum” cryptography.
One example of a post-quantum cryptographic algorithm is lattice-based cryptography. These algorithms are based on the complexity of certain mathematical problems in lattices, which are mathematical structures formed by discrete points in a multi-dimensional space. Lattice-based algorithms are believed to be resistant to quantum attacks, as they do not rely on the computational infeasibility of certain mathematical operations (such as factoring large numbers) that are vulnerable to quantum attacks.
Another example of a post-quantum cryptographic algorithm is multivariate cryptography. These algorithms are based on the complexity of solving systems of multivariate polynomial equations, which are difficult to solve even with a quantum computer.
It is important to note that post-quantum cryptography is still an active area of research. It is unclear which algorithms and protocols will ultimately be the most effective at resisting quantum attacks. Different post-quantum algorithms and protocols will likely be needed to provide robust security against quantum computers.
What are the best practices and architectures for implementing a web application firewall?
There are several best practices and architectures for implementing a web application firewall (WAF):
- Choose a WAF that meets the organization’s needs: It is important to select a WAF that is appropriate for the size, complexity, and security needs of the web application and the organization. This may include considering factors such as the type of web application, the level of security required, the available resources for deployment and maintenance, and the budget.
- Use a multi-layered defense: A WAF should not be the only security measure to protect a web application. Instead, organizations should use a multi-layered approach that includes secure coding practices, regular security assessments, and incident response planning.
- Configure the WAF to decrypt and inspect encrypted traffic: If attackers are using SSL/TLS encryption to hide their attacks, the WAF will not be able to detect and block them unless it is configured to decrypt and inspect encrypted traffic.
- Regularly review and update WAF rules: It is important to regularly review and update the rules and patterns used by the WAF to ensure that they are effective at detecting and blocking a wide range of attacks. This may include adding new rules to detect emerging threats, as well as testing existing rules to ensure that they are functioning correctly.
- Use a WAF with machine learning capabilities: Some WAFs use machine learning algorithms to learn and adapt to new attacks in real-time. This can help protect against attackers who try to bypass the WAF by using novel or previously unseen tactics.
- Monitor the WAF and the web application: It is important to monitor the WAF and the web application for signs of attacks or vulnerabilities. This may include reviewing logs, monitoring traffic patterns, and conducting regular security assessments.
- Test the WAF: It is important to test the WAF to ensure that it is functioning correctly and providing the desired level of protection. This may include conducting penetration tests, load testing, and other types of testing to ensure that the WAF is effective at detecting and blocking a wide range of attacks.
Table of Contents
 Copyright secured by Digiprove © 2022-2023
Copyright secured by Digiprove © 2022-2023 
